IBM i Multi-Factor Authentication (MFA) is a critical cybersecurity defense required by PCI, FFIEC and 23 NYCRR 500 in Section 500.12b, stating any company providing financial services within the state of New York must implement MFA to protect system data and applications for all users that have external network access, or use an approved access control equivalent. IBM i Multi Factor Authentication prices are very affordable, simple to implement and provide the quickest means to protect against the cybersecurity threats 23 NYCRR 500 was drafted to address. IBM i 2FA, Two-Factor Authentication is the same as MFA and Multi-Factor Authentication. Why...
IBM i Two-Factor Authentication (2FA) is a quick and simple to implement Multi-Factor Authentication solution that ensures a user’s identity before granting access to critical or sensitive data on your system. IBM i 2FA can be enforced for various connection types, including interactive 5250 telnet signon sessions, and for most TCP/IP connections where users logon thru an exit point, such Database Server for ODBC and JDBC connections, Signon Server, FTP Server and File Server for accessing the IFS, which can help prevent ransomware and other forms of malware from damaging your system. IBM i MFA can also be used for securing SSH...
SFTP and FTPS are Secure File Transfer methods the IBM i (AS400 iSeries) supports natively for both client and server roles, and can safely transfer sensitive files to and from any other platform or cloud service. Secure FTP requirements may dictate which protocol (SFTP versus FTPS) for the Managed File Transfer (MFT) project, but is usually a user preference. Both SFTP and FTPS use encrypted connections for file transfer, SFTP uses SSH cryptographic protocol and FTPS can use TLS or SSL implicit security (always on) cryptographic protocol. FTPS explicit can also be used, but it is not recommended for secure file...
File integrity monitoring FIM for IBM i requires monitoring the system security audit journal and DB2 database journals to detect unauthorized changes to files and their contents. FIM projects are usually due to compliance regulations such as PCI, 23 NYCRR 500 and like regulatory requirements, which will significantly reduce the file integrity monitoring scope to specific database files and object changes in QAUDJRN. In addition to implementing file integrity monitoring, you will need to ensure user authorities and access control policies are correctly defined and monitored for changes going forward. On an iSeries, many of these settings can be defined from the...
Implementing iSeries Profile Swapping and Adopted Authority policies is a great idea for reducing the number of powerful profiles on the IBM i, especially if most users only need elevated authority for specific tasks or occasional access to sensitive data. On the IBM i (iSeries AS400), the Profile Swapping, Adopted Authority and Elevated Authority procedures are more commonly referred to by compliance regulations and other platforms as Privileged Access Management (PAM) proceedures. However these processes ultimately have the same objective, limiting the number of user profiles on the iSeries that possess unnecessary special authorities (or having a powerful user classes or have no...
General Data Protection Regulation GDPR data protection law applies to any company that transmits, store or process personal data of in...
Cybersecurity breaches caused by employees account for roughly 75% of all data breaches. Internal security threats are usually among the costliest att...
iSeries MFA provides Multi-Factor Authentication to prevent unauthorized user access to systems by adding two or more authentication require...
The QRadar SIEM app list grew even larger last month with the addition of 2 more cybersecurity vendors. Varonis Systems, Inc., a pioneer in data secur...
Webroot just released their latest cybersecurity threat report after analyzing data from the first half of 2018, and results show hardware can be just...
QRadar SIEM Security Intelligence Platform is recognized as a Leader for the 10th consecutive year in the latest Forrester comparison report "Wave on ...
QRadar Cloud Visibility app on the x-Force app exchange is for managing and providing security for Amazon Web Services, Microsoft Azure...
QRadar TruSTAR's app enables ingestion of OSINT, 3rd party cybersecurity threat intelligence, ISAC/ISAO feeds and your own internal data in...
Cybersecurity AI integrated SIEM Security tools accurately identify and prevent attacks in a fraction of the time and cost humans are capable, using s...
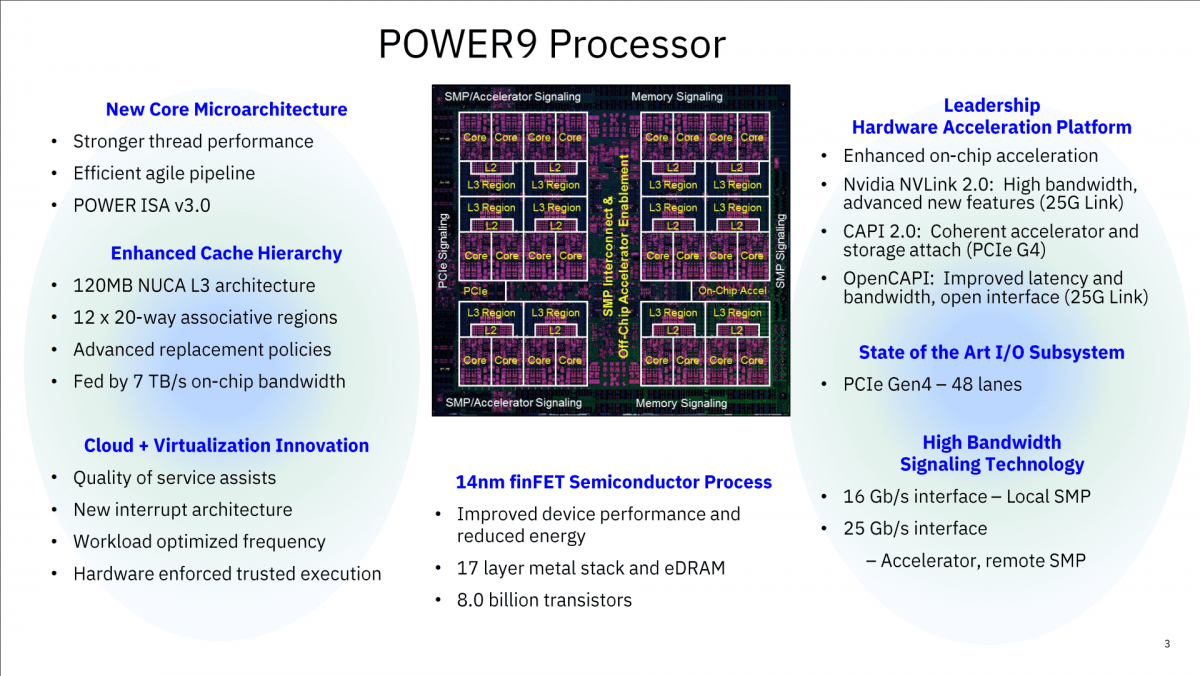
POWER9 Memory changes and what it means. Our last article was about the primary changes made to the POWER Systems, scale out line up with the rel...
This is the first of a series of short videos on the SIEM and SYSLOG forwarding tool for the AS400 platform… or iSeries IBM i if you prefer.This first...