Immutable backup technology is a critical component for Cyber Resiliency and Disaster Recovery for organizations of any size. As for an IBM i backup copy, there are additional options for immutable backups and SafeGuarded Copy solutions. Cyber resilience is a measure of an organization’s ability to protect data and continue business operations despite a successful cyberattack involving data that is either corrupted or destroyed, such as from a malware or ransomware attack. The measure of cyber resiliency is based on amount of data loss and recovery time required to resume normal business operations. If you were to conduct a cyber resiliency...
Protecting the IBM i Integrated File System IFS from ransomware and other forms of malware can be a fairly quick process, and there are a number of simple steps you can take to minimize your systems’ vulnerabilities to prevent a successful attack. You should be aware, viruses, ransomware and other forms of malware do not run on the IBM i, however these threats can severely wreak havoc on the IBM i as a result of a few common security vulnerabilities that can often be resolved with a few simple changes. Other IBM i environments will have to take additional security measures...
An advanced Enterprise Job Scheduler designed to automate intricate job scheduling tasks across any mid-range platform, database and application. This powerful portable batch system offers centralized job scheduling management and remote control capabilities, capable of streamlining all scheduling processes across your entire organization worldwide. The Enterprise Job Scheduler supports native installation in every midrange environment, including IBM i (iSeries AS400), Windows, Linux, AIX, HP-UX and Solaris environments - ensuring optimal throughput, accuracy and efficiency. The Enterprise Job Scheduler serves as a portable batch system which can be used for single platform use cases, such as an IBM i job scheduler, offering a...
Screen Capture for IBM i is a feature of the Authority Manager that automates monitoring users performing sensitive tasks or those needing special authorities to perform specific tasks in a controlled and fully auditing environment. The IBM i Screen Capture feature takes a screen shot of each screen the user is on and includes all the user entered text, and saves the screen shot in a searchable pdf and log on the IBM i. The IBM i Authority Manager enables monitoring powerful users via rules that ensures ticket numbers are used for assigned tasks, auditing and screen capture is enabled, and...
Upgrading your IT infrastructure doesn’t have to be a headache. At Midland, we’re here to take the stress out of the process and ensure you get the right solution for your business. Whether you're considering an IBM Power10 upgrade to boost performance and scalability or simply looking to maximize your investment, we make it straightforward, efficient, and hassle-free. With our expert guidance and the right preparation, your first call with Midland can set the stage for a smooth upgrade experience. Here’s everything you need to know to get started—and how we’ll help make the process seamless every step of...
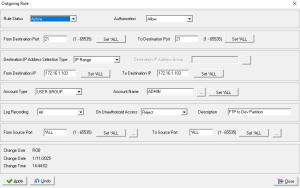
AS400 Firewall Manager is a software based firewall that runs natively on the IBM i that enables administrators to define incoming and outgoing access policies based on Ports, IP Addresses, and logical groups of which AS400 Network Segmentation policies can be applied for the types of traffic that may flow in and out of the IBM i. The AS400 Firewall Manager uses AS400 exit programs to control traffic, and provides a simple point and click GUI interface to define policies. The AS400 exit program for the QIBM_QSO_ACCEPT exit point is used to monitor and control incoming traffic and a separate exit...
IBM i SIEM Security Event Logs for Monitoring Companies using Splunk, QRadar or any other SIEM to monitor security incidents, of which also run core business applications on an IBM i, should be forwarding specific data sets and event log sources to their SIEM. Most companies with an IBM i (AS400 or iSeries), often have their most critical business applications running on it, yet the AS400 is commonly the last platform to be added to the SIEM. Security Operation Center Administrators and Architects often underestimate the importance the AS400 and its underlying applications are to their company, or disregard it due...
Table Of Contents Chapter 1: Introduction to Managed SIEM 7 What is Managed SIEM? 7 Benefits of Managed SIEM 10 Challenges in Implementing Managed SIEM 13 Role of Managed SIEM in Cybersecurity 15 Chapter 2: Managed SIEM - Definition & Overview 18 Understanding SIEM (Security Information and Event Management) 18 Evolution of Managed SIEM 20 Key Components of Managed SIEM 24 How Managed SIEM Works 27 Advantages of Managed SIEM over In-house Solutions 29 Chapter 3: Cloud Managed SIEM 32 Introduction to Cloud Managed SIEM 32 Benefits of Cloud Managed SIEM 33 Challenges in Implementing Cloud Managed SIEM 34 Features and...
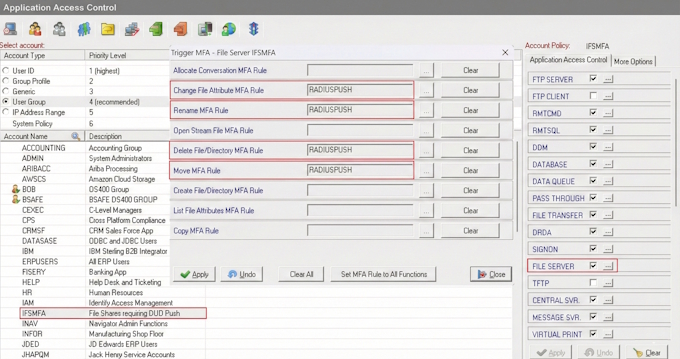
IBM i Two-Factor Authentication (2FA) is a quick and simple to implement Multi-Factor Authentication solution that ensures a user’s identity before granting access to critical or sensitive data on your system. IBM i 2FA can be enforced for various connection types, including interactive 5250 telnet signon sessions, and for most TCP/IP connections where users logon thru an exit point, such Database Server for ODBC and JDBC connections, Signon Server, FTP Server and File Server for accessing the IFS, which can help prevent ransomware and other forms of malware from damaging your system. IBM i MFA can also be used for securing SSH...
IBM i Multi-Factor Authentication (MFA) is a critical cybersecurity defense required by PCI, FFIEC and 23 NYCRR 500 in Section 500.12b, stating any company providing financial services within the state of New York must implement MFA to protect system data and applications for all users that have external network access, or use an approved access control equivalent. IBM i Multi Factor Authentication prices are very affordable, simple to implement and provide the quickest means to protect against the cybersecurity threats 23 NYCRR 500 was drafted to address. IBM i 2FA, Two-Factor Authentication is the same as MFA and Multi-Factor Authentication. Why...
SFTP client software or Secure FTP that uses SSH (Secure Shell) and PGP encryption for secure file transfer over the SSH2 protocol as defined by the Internet Engineering Task Force (IETF) SSH (SECSH) working group. Customers with an AS400, iSeries or IBM i can use the Secure FTP (SFTP) to automate secure file transfers to their bank or other trading partners in just a few minutes. Banks like Bank of America, BankOne, CitiGroup, JP Morgan Chase, State Street, US Bank, Vanguard and Wells Fargo have additional file transfer requirements such as PGP encryption, ASCII armored, RSA public key exchange, sign and verify, key...
From its inception in the 1980s, the IBM AS400 and OS400 operating system has had many iterations and transformations over the years, but it has consistently maintained the distinguished honor of delivering businesses the lowest TCO midrange computing system in the industry. To this day, tens of thousands of businesses, including the largest companies in the world rely on the IBM i to run their most critical applications. There is no single reason, but collectively, the entire IBM i package of hardware, operating system, integrated database and all the features they encompass and provide businesses, is what contributes to the extremely...
SFTP and FTPS are Secure File Transfer methods the IBM i (AS400 iSeries) supports natively for both client and server roles, and can safely transfer sensitive files to and from any other platform or cloud service. Secure FTP requirements may dictate which protocol (SFTP versus FTPS) for the Managed File Transfer (MFT) project, but is usually a user preference. Both SFTP and FTPS use encrypted connections for file transfer, SFTP uses SSH cryptographic protocol and FTPS can use TLS or SSL implicit security (always on) cryptographic protocol. FTPS explicit can also be used, but it is not recommended for secure file...
It has only been a year, and the new data protection and privacy regulations have already hit a few companies with multi-million dollar fines. Every company with sensitive data on an IBM i (iSeries AS400) and has data protection and privacy requirements, should have implemented DB2 encryption already. Some of the companies seen in the news recently not only failed to secure personal data properly, could not accurately assess how much data was compromised, had a lax incident response plan and were slow to notify authorities. These factors all led to heavier fines, causing the total financial penalties to exceed 100s...
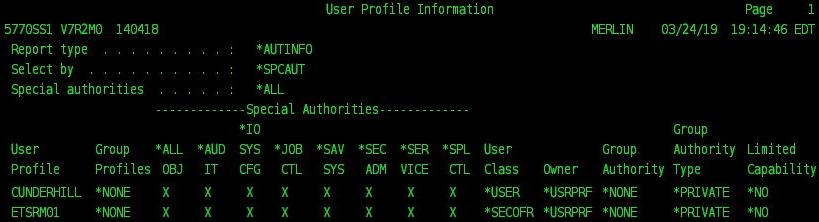
Security breaches making headlines are almost always due to inadequate access controls at one or more levels of a company’s infrastructure. Known and unknown vulnerabilities may have assisted in most security breaches that we read about, but most could have been avoided with the proper security access controls implemented, or at least significantly mitigated. The IBM i security framework is not immune to breaches and certainly not the most secure platform in your environment if the necessary access controls have not been implemented. All compliance regulations have general guidelines to implement various forms of access controls, including stricter authentication policies using Multi-Factor Authentication (MFA), Profile...
IBM i Privileged Access Management (PAM) solutions have various levels of flexibility for implementation and integration with existing applications and ticketing systems that need to be considered before purchasing. Assessing your IBM i Security requirements for implementation will be key to ensuring the IBM i PAM solution you choose meets your all your use cases, as well as environmental and compliance requirements. First note, Privileged Access Management (PAM) terminology used by most technology sectors and compliance regulations refer to processes more commonly known on the IBM i (iSeries AS400) platform as Profile Swapping and Adopted Authority procedures. Terminology aside, the goal of...
Configuring the IBM i to forward security and system event logs to QRadar SIEM can be done a few different ways, but in order to do it correctly; in LEEF format, in real-time, with GID and enriched event log information, you need an IBM i event log forwarding tool designed for the QRadar SIEM. There are IBM i security event log forwarding tools that can be used for QRadar that will send event logs in real-time and in CEF SYSLOG format, and even a couple that support LEEF, but only one includes QRadar QID for mapping, log enrichment and is on...