AS400 Network Segmentation: Firewall Manager
AS400 Firewall Manager is a software based firewall that runs natively on the IBM i that enables administrators to define incoming and outgoing access policies based on Ports, IP Addresses, and logical groups of which AS400 Network Segmentation policies can be applied for the types of traffic that may flow in and out of the IBM i. The AS400 Firewall Manager uses AS400 exit programs to control traffic, and provides a simple point and click GUI interface to define policies. The AS400 exit program for the QIBM_QSO_ACCEPT exit point is used to monitor and control incoming traffic and a separate exit program for the QIBM_QSO_CONNECT exit point monitors and control outgoing traffic.
AS400 network security controls provided by typical or common exit programs, such as those used to monitor and control users access of Database Server for ODBC and JDBC applications, File Server for IFS, SignOn Server and FTP, most often provide adequate security controls to satisfy the requirements for most IBM i environments. However, there are a few scenarios where the additional layer of security offered by the AS400 Firewall Manager are needed. The first that comes to mind are AS400’s that are hosted off premises in another company’s data center, such as a cloud environment. The other scenario would be companies that are implementing Network Segmentation policies that want to incorporate the AS400 into the Network Segmentation schema. The last and more abundant reason would be to secure connections that cannot be monitored or controlled as easily, like sFTP (SSH) connections. Although the AS400 Firewall is a great solution for monitoring and controlling these connections, it is recommended to secure sFTP (SSH) connections with Multi-Factor Authentication using IBM i MFA.

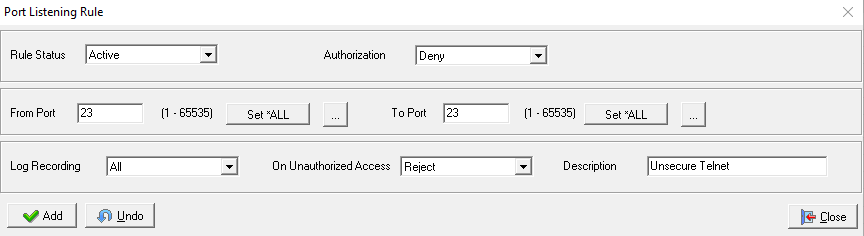
The AS400 Firewall Manager also allows administrators to define Port Listening policies for maintaining compliance status, such as ensuring non-secure ports are never listening. AS400 Port Listening rules are also enforced by an exit program, which monitors and controls the QIBM_QSO_LISTEN exit point. The Port Listening exit program is the simplest of the three, of which either allows or denies the socket’s ability to listen for new connections.
The three exit programs used by the AS400 Firewall Manager are categorized as socket exit programs, a terminology adopted by the previous implementation or technology IBM created for IP Packet Filtering rules, which was depreciated many OS versions ago. The AS400 Firewall Manager’s socket exit programs gives administrators’ very powerful functionality to implement complex network security rules very quickly and safely. By ‘quickly’, I also mean easily. Like typical or traditional exit programs, socket exit programs provide an additional layer of security for the IBM i that hardware based Firewalls and Routers cannot, and enforced before application access control layers.
How the AS400 Firewall Works for IBM i:
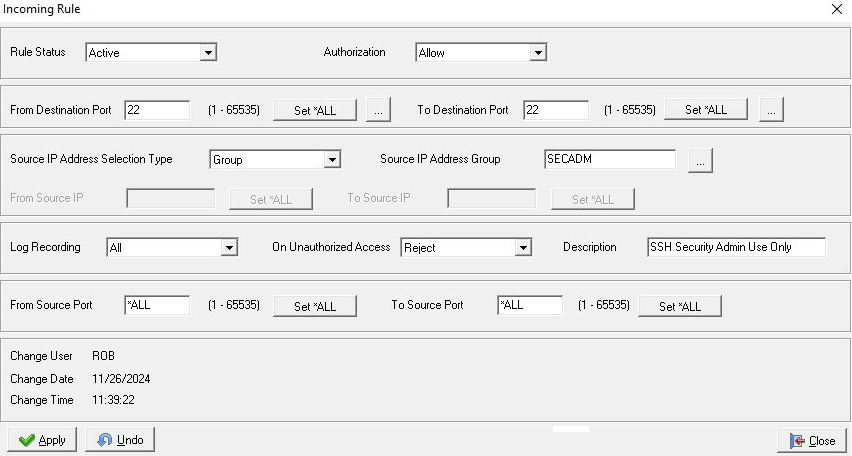
The AS400 Firewall Manager can monitor and secure all inbound and outbound TCP/IP connections to your IBM i. Incoming access control policies can be defined by rules for a source’s IP Address, IP Address Range or Groups of IP Addresses and Ranges. Each incoming source rule determines the destination Port or Port Range on the AS400 that can be used by the source(s). The rule will also determine if the Access should be allowed or rejected, as well as if logging should be enabled or not. Outgoing polices work similarly, with the additional ability of defining User and User Group based policies. Since connections from a source are made before a user enters their logon credentials, Incoming rules obviously cannot utilize User based policies.
It is important to note, IBM does not allow incoming rules for Port 23, or UDP ports such as TFTP and SNMP. In addition, Port Listening rules for UDP ports such as TFTP and SNMP are ignored, and Port 445 with SMBSERVERMAIN cannot be enforced. Other than these limitations, the AS400 Firewall Manager can audit and lockdown any port for incoming and outgoing IBM i traffic for OS400 version V7R1 and higher. IBM does not have any outgoing rule limitations.
Summary of benefits:
- Quick and easy to set up and maintain. Simple point and click administration means no special training required.
- Implement safely and with confidence. Simulation mode allows traffic to be monitored via logs or reports before making decision to reject.
- Real-time intrusion detection alerts for policy infractions and suspicious activity.
- Adopt AS400 Network Segmentation policies that align with corporate policies and enforce compliance requirements.
- Fully integrated into Enforcive Enterprise Security suite for User and User Group policies and reporting.
- Predefined reports with detailed auditing, distributed via email and archived on IFS desired format.
- Complete visibility of all network traffic in and out of IBM i.
- Flexible controls for incoming and outgoing network traffic.
- Simple port listening policies that cannot be changed.
- Monitor and Control network traffic that avoids common ‘traditional’ exit points, such as IBM i Navigator, sFTP (Secure Shell SSH), FTPs (SSL/TSL), newer and lesser known protocols.
- Expands current HW firewall functions
- Dedicated control for IBM i traffic
- Enhanced user profile based policies
- Blocks network traffic that avoids exit points
- Provides function/command information
