Is it the right time for you to get a small business server? While the process of growth within small businesses can be exciting, business owners are often faced with technology pains that accompany a growing team. With more people come more computers and the once effective peer-to-peer method of managing computers when there were just a handful of people no longer proves to be effective or sustainable. With this growth in your business, it may be time to consider getting a small business server. If you are beginning to manage a small fleet of computers that share printers, scanners, internet...
IBM Linux server hardware performance and software license costsThe best Linux server hardware for enterprise open-source ecosystems will be the platform that delivers the best processor, memory and disk performance per core. Judging by the number of discussions in customer support communities, technical articles and blog posts on various Linux server performance troubleshooting, there is clearly a need for a better performing Linux server for both scale up and scale out infrastructures. This article will explain the importance of selecting the best performing hardware for your Linux server farm and how it affects software license costs. IBM POWER10 and IBM POWER9 Linux...
IBM Power9 Servers may be the best Linux server to run your applications. IBM Power Linux servers have a proven history of delivering over twice the performance per core compared to industry leading x86 server brands. IBM Power Linux servers have also proven to deliver the lowest cost of ownership compared to other Linux servers running on x86 hardware. Although there is no one single answer to this question, the two statements address what most people want to know when comparing Linux server workloads, such as: application server, database server, cloud server, SAP server, analytics server, business intelligence server, web...
SFTP client software or Secure FTP that uses SSH (Secure Shell) and PGP encryption for secure file transfer over the SSH2 protocol as defined by the Internet Engineering Task Force (IETF) SSH (SECSH) working group. Customers with an AS400, iSeries or IBM i can use the Secure FTP (SFTP) to automate secure file transfers to their bank or other trading partners in just a few minutes. Banks like Bank of America, BankOne, CitiGroup, JP Morgan Chase, State Street, US Bank, Vanguard and Wells Fargo have additional file transfer requirements such as PGP encryption, ASCII armored, RSA public key exchange, sign and verify, key...
IBM recently introduced their newest POWER servers with the POWER9 processor to the marketplace. Has your business has been debating staying on the IBM i platform instead of migrating your data to the cloud or to another OS platform like Linux Servers or another x86 server solution? You really should consider the benefits of the latest POWER9 systems are and IBM i 7.4. The AS400 iSeries POWER lineup of servers has long held a reputation for reliability and security. IBM i is all about integration and innovation. Businesses running high-traffic, mission-critical applications are deploying IBM Systems in their own data centers and in...
From its inception in the 1980s, the IBM AS400 and OS400 operating system has had many iterations and transformations over the years, but it has consistently maintained the distinguished honor of delivering businesses the lowest TCO midrange computing system in the industry. To this day, tens of thousands of businesses, including the largest companies in the world rely on the IBM i to run their most critical applications. There is no single reason, but collectively, the entire IBM i package of hardware, operating system, integrated database and all the features they encompass and provide businesses, is what contributes to the extremely...
Midland is proud to offer Infrastructure as a Service (Iaas), starting at $525 per month to allow for continuing business operation of customers in the event of a disaster or unplanned outages for IBM POWER systems. Midland will provide an onsite IBM POWER server that will be scalable with processor (CPW), memory and disk. Your production systems will be replicating to the disaster recovery system and Group33 will manage replication. Disaster Recovery Starting at $525 mo. All of our systems will be hosted on site at Midland. We can offer an affordable solution by providing 9 to 5 support during normal...
POWER System upgrades are often among the most prolonged and undervalued IT decisions. Why rush to invest in a POWER9 upgrade when your POWER7 or POWER8 server performance is perfectly fine? Truth is: over a 5-year span you may waste a good amount of cash maintaining those legacy systems instead of capitalizing on the true cost savings and many additional benefits a POWER9 server offers. Not a believer? Well here are the facts.Why Regular Hardware Updates Actually Save You MoneyLegacy IT modernization isn’t a persistent budget drain. On the contrary, regular updates save you a hefty sum in the long run....
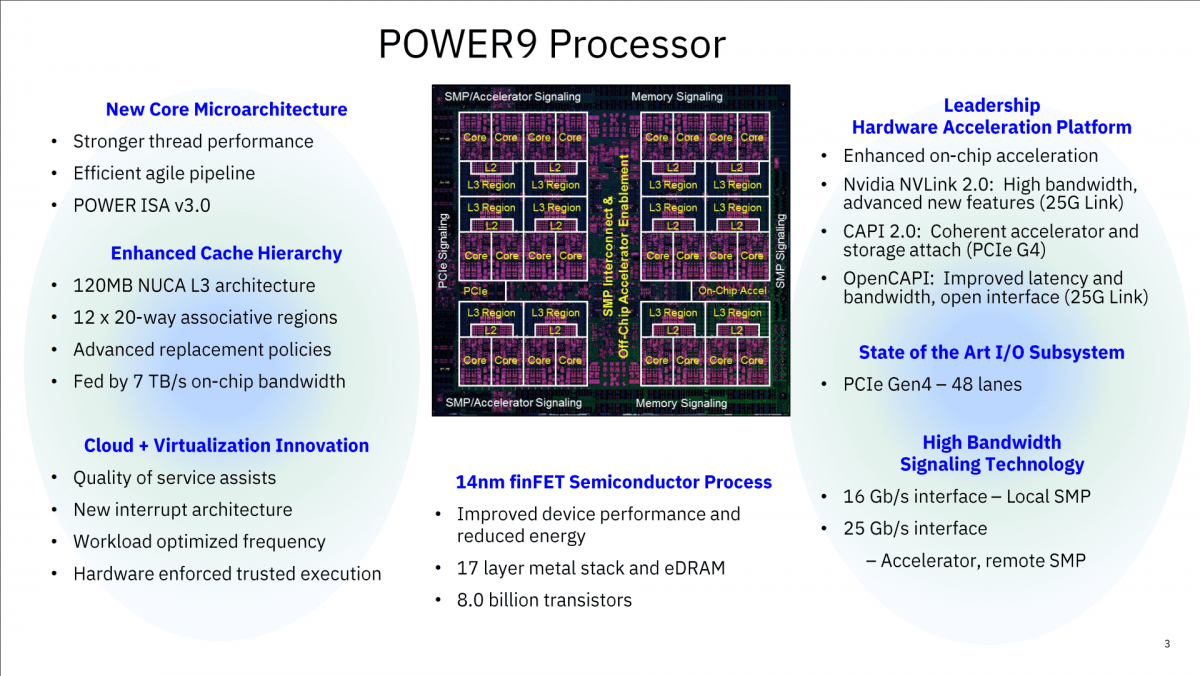
POWER9, IBM’s latest family of scale-up servers, has been around since August 2018. Since it’s debut, they received several new members, along with other hardware upgrades. In this post, we offer a quick recap of the new IBM releases in 2019, along with the outlook for 2020. Before we dive into the updates, here’s a quick refresher on POWER9: New chips come with a 14 nm process (from 22 nm in POWER8), 8 billion transistors and peak bandwidth of 192 GB/s. The pipeline got a trim: 5 stages were eliminated from fetch to compute; 8 cycles were removed for floating-point operations....
How to increase IBM POWER System application performance running on IBM i, AIX and Linux Server with SSDs (Solid State Drives) Every IBM POWER System application performs significantly faster running on SSD (microsecond and nanosecond response times, compared to millisecond and seconds). Application performance on IBM POWER Systems experiencing slow query responses times, have intensive I/O requirements or are experiencing latency as a result of accessing data on hard disk drives, can improve performance using various database and query approaches. However, the most effective and usually quickest approach is to replace traditional HHDs with IBM Solid State Drives (SSD) using either Enterprise or...
Managed SIEM Services (MSIEM, SOCaaS, MSSP, SIEMaaS) can provide companies with various levels of security services at a reasonable price including: Monitoring (threat hunting), vulnerability scanningReporting, alertingRoot cause analysisData encrichment and intelligence providing context about security incidentsRecommendations for containment and remediation stepsPerform actual remediation on behalf customerSIEM tuning and managed security services needed to augment deficiencies in expertise and staffing. Managed SIEM prices vary based on the volume of events per second (EPS) and the required level of services from the SIEM as a Service provider. To compare apples to apples, be sure to request a detailed SOW and clear SLA. Outsourcing SIEM...
The IBM Hardware Management Console (HMC) is a virtual hardware appliance used to manage and monitor IBM i, AIX and Linux server workloads running on Power9, Power8, Power7, Power6 and Power5 Systems. The IBM HMC uses built in terminal emulation software to connect and control Power system resources, services, virtualization features and order Capacity Upgrade on Demand. The IBM HMC can consolidate the monitoring and management of all Power systems in a company’s infrastructure that is supported by the HCM code. Every HCM model supports different Power system models based on the version of HMC code. For instance, the latest HCM...
Is your SIEM the magic bullet? Many companies are finding their SIEM implementations have provided little return on investment and have not strengthened their security posture to any great degree. Purchasing the best SIEM and endpoint security tools on the market will not magically identify vulnerabilities, make an infrastructure more secure. Every SIEM requires proper implementation and ongoing tuning services to keep up with the constant changing landscape of threats, vulnerabilities and a customer’s own environment. Like any security product, every SIEM requires an experienced technician to configure it correctly, and enough staff must be trained to keep up with the volume...
It has only been a year, and the new data protection and privacy regulations have already hit a few companies with multi-million dollar fines. Every company with sensitive data on an IBM i (iSeries AS400) and has data protection and privacy requirements, should have implemented DB2 encryption already. Some of the companies seen in the news recently not only failed to secure personal data properly, could not accurately assess how much data was compromised, had a lax incident response plan and were slow to notify authorities. These factors all led to heavier fines, causing the total financial penalties to exceed 100s...
Most SIEM environments rely on a plethora of different servers, storage arrays, hypervisors and network interconnects to support their rapidly growing SOC environments. Likewise, most SIEMs also all have the same issues and concerns about performance, costs and time required to provision and manage storage growth. The primary problem is, the entire infrastructure the SIEM relies on is not integrated or even truly virtualized under a single unified architecture. As a result, administrators are stuck in a never ending battle of upgrading and adding more traditional technology for the same problems, and security analysts are constantly waiting for searches to complete...
Details of each POWER9 and POWER8 hardware enhancement provided by the release of IBM 7.4 (V7R4) are below the initial summary, organized by IBM Power generation and topic. The new IBM POWER9 and POWER8 hardware features provided for OS400 V7R4 are now all available for ordering as of June 21, 2019. Read about IBM i 7.4 (V7R4) announcement details here. IBM V7R4 announcement provides the following I/O enhancements for Power9 scale-out and scale-up system models: 1.6 TB, 3.2 TB, and 6.4 TB PCIe3 Enterprise SSD NVMe adapters for Power9 E980, E950, L922, S922, S914, S924, H922, and H924 servers1.6 TB and...
QRadar Prices for All-in-One SIEM Appliances start at $38,500.00 to $102,000.00. Pricing is calculated based on the volume of events and network flows ingested by the SIEM. QRadar prices for All-in-One appliance includes the following licenses for out of the box deployment: Maximum Events per Second defined by model (expandable increments: 100, 500, 1000, 2500, 20000, 40000, 80000)Maximum Flows per Minute defined by model (expandable increments: 10000, 25000, 50000, 100000, 1200000, 2400000, 3600000)QRadar Security Intelligence Console for SOC including advanced threat protection, predefined dashboards, partner provided and editableIBM Security AI Sense Analytics for assets on premise, mobile, remote sites and cloud servicesAsset...
IBM i V7R4 (7.4) OS400 enhancements and additions improve Power9 and Power8 system and DB2 database performance, security and availability. Details of OS400 V7R4 features and specifications for IBM i Power Systems are explained below in detail, and arranged by the following topics: Security, System Management, Networking, Availability, Application development, Miscellaneous features. IBM i V7R4 (7.1) release date is June 21, 2019. OS400 V7R4 is supported on IBM Power9 and Power8 processor systems, and is not supported on earlier IBM Power system processor generations. All IBM i customers should read the IBM 7.4 memo before upgrading to ensure compatibility and verify if discontinued...
This QRadar vs Splunk comparison will help anyone planning on switching in 2019 from Splunk to QRadar SIEM. It will also help anyone just curious to s...
A hyper converged infrastructure (HCI) uses software to virtualize all server and storage resources for streamlining, automating and maximizing IT resources and operations for a variety of complex, compute-intensive Databases, VDI, Microsoft, Business Applications, Cloud, Big Data, SIEM, SYSLOG and other x86 environments. HCI virtualization solutions significantly reduce operating and licensing costs, provide predictable performance, provide up to 2.8 times storage gains and enables long-term flexibility and scalability. The HCI software defined infrastructure model addresses almost every IT challenge facing companies today, including:Improving IT staff productivityImproving operational efficiencyReducing capital expensesReducing operating expensesImproving backup/recoveryImproving resource utilizationData center consolidationThe value of hyper converged infrastructure...