Configuring the IBM i to forward security and system event logs to QRadar SIEM can be done a few different ways, but in order to do it correctly; in LEEF format, in real-time, with GID and enriched event log information, you need an IBM i event log forwarding tool designed for the QRadar SIEM. There are IBM i security event log forwarding tools that can be used for QRadar that will send event logs in real-time and in CEF SYSLOG format, and even a couple that support LEEF, but only one includes QRadar QID for mapping, log enrichment and is on...
IBM i Privileged Access Management (PAM) solutions have various levels of flexibility for implementation and integration with existing applications and ticketing systems that need to be considered before purchasing. Assessing your IBM i Security requirements for implementation will be key to ensuring the IBM i PAM solution you choose meets your all your use cases, as well as environmental and compliance requirements. First note, Privileged Access Management (PAM) terminology used by most technology sectors and compliance regulations refer to processes more commonly known on the IBM i (iSeries AS400) platform as Profile Swapping and Adopted Authority procedures. Terminology aside, the goal of...
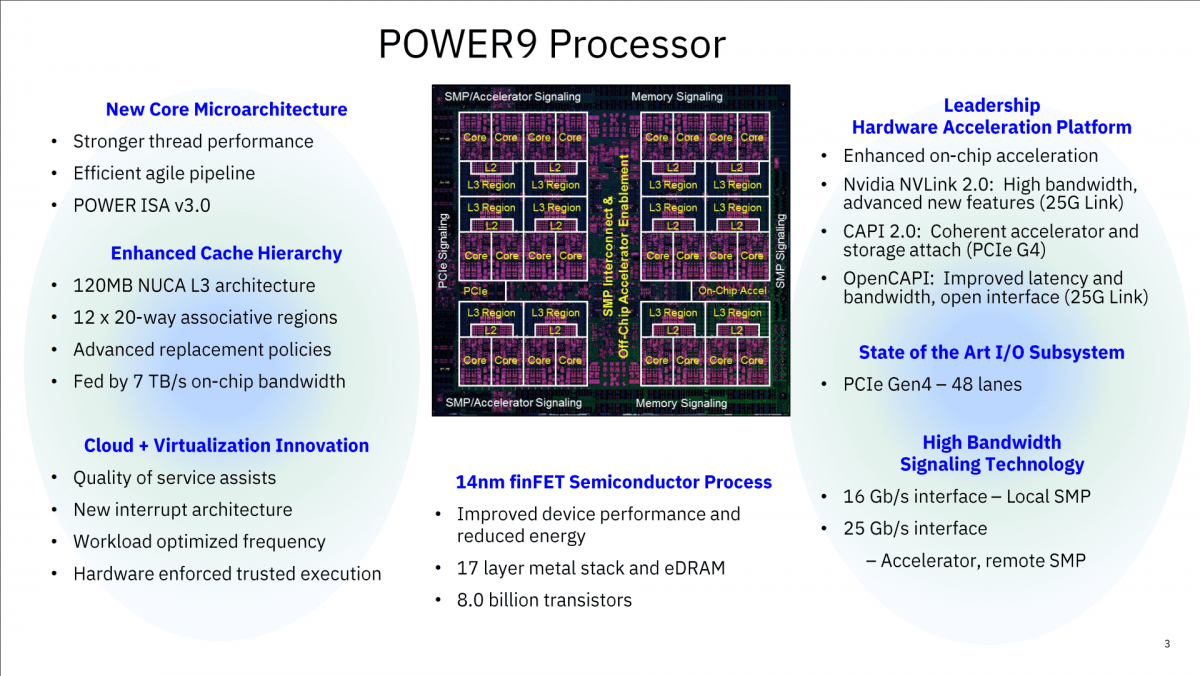
IBM i customers upgrading to a new IBM Power9 scale-out system from an older Power system have three models to compare specifications; the 9009-41A S914, 9009-42A S924 or 9009-22A S922. Before jumping to any conclusions about which Power9 system is right for you, consider the specifications and resources of your current IBM i and performance during peak times. The new Power9 systems are so powerful, many companies are finding they can drop a software tier without any question. Dropping an IBM P-Group in itself is a significant cost savings, and the total cost of ownership price tag adds up after factoring...
Share this post: There are many misconceptions about IBM Power Systems in the marketplace today, and this blog series will help to dispel some of the top myths. In my previous post, I put aside the myth that migrating from x86 to IBM Power Systems is costly, painful and risky. In this post, we’ll look at another myth suggesting that x86 architecture is the de-facto industry standard for all applications and that Power Systems will soon become obsolete. Myth versus reality To begin breaking down this myth, let’s consider how IBM Power Systems stands apart from x86. Designed for enterprise workloads....
Keeping your IBM i optimized for optimal response times requires regular monitoring of system resources and identifying various elements that affect application performance. Poor response times of only two or three seconds delay can quickly get compounded over time when poorly written applications are involved or database maintenance has been neglected. Like most performance degradation issues on the IBM i, response time issues only get worse as the number of transactions multiply. Ignoring system performance issues affects productivity and frustrate customers, which in turn increases costs and affects revenue. Below are some ideas to consider if a major IBM i upgrade...
*Also see QRadar Pricing on all IBM SIEM Security Intelligence Product Prices (including QRadar Hardware Appliances) QRadar SIEM Free Trial Compared to what you are doing today, QRadar will unify your existing IT infrastructure and security products into a user friendly and intelligent SOC. QRadar provides advanced, automated threat detection above and beyond what you would expect. But the only way to appreciate the simplicity and robustness of QRadar SIEM platform is to evaluate security solution for yourselves. QRadar FREE Trials & Demos 2023 QRadar Manufacturer Suggested Retail Price Chart by License*MSRPQRadar SIEM by IBM Security - Event Processor Virtual 1690...
IBM EJ14 PCIe3 12 GB Cache RAID Plus SAS Adapter is the highest performing raid controller (SAS adapter) for IBM Power9 and Power8 systems that will significantly improve raid performance. The IBM EJ14 PCIe3 12 GB Cache RAID PLUS SAS Adapter has four 6 Gb connectors enabling the highest performance HDD or SSD SAS controller capabilities for IBM Power systems using PCIe Gen3 technology and IBM’s latest SAS RAID adapter technology. The EJ14 PCIe3 SAS adapter builds on the success of the EJ0L PCIe3 12 GB Cache RAID SAS Adapters, but delivers up to 100% more write IOPs than the older EJ0L...
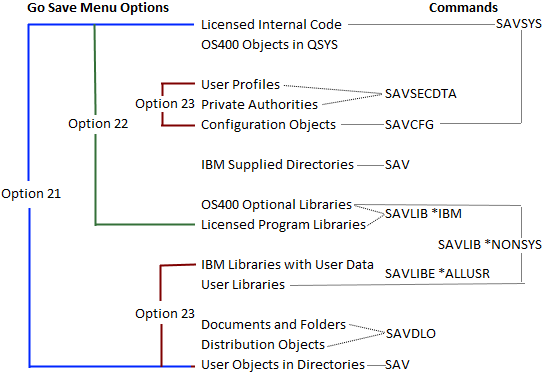
IBM i backup performance is affected by many variables, and many data transfer rate bottlenecks can be very easy to resolve. Some simple changes you can try to improve IBM i backup performance may only require simple changes like using the correct media generation for your tape library or tape drive, minimize resource sharing, shortening the distance between the IBM i PCIe I/O adapter and tape library/drive, using backup optimization settings or restructuring your backup processes. These minor changes are virtually free to try and may have a significant impact on optimizing your IBM i backup transfer rates and without having...
The IBM z mainframe system remains the workhorse for most of the largest and most successful companies in the world, maintaining both mission critical legacy software applications and new workloads. In the scope of sensitive data and security, the IBM z/OS protects the company’s jewels for good reason, but has a plethora of system and security event log sources that must be monitored and forwarded to a SIEM like IBM QRadar, AlienVault, Exabeam, Managed SIEM or a SYSLOG Server like the Splunk. Since IBM mainframe event logs do not conform to SIEM and SYSLOG industry standards, many IBM z shops are running batch...
IBM mainframe systems are still running the bulk of critical workloads at over 70% of the world’s largest and most successful companies. The first IBM mainframe and 911 Porcshe were both sold in same year, 1964. Most people do not realize how advanced and powerful the IBM z platform is, and always has been. The fact is, virtualization was being developed on the IBM mainframe in the 1960s and added this amazing new technology to the platform in 1972, decades before any other platform. To this day, companies are adding more and more workloads to their IBM z every day, because...
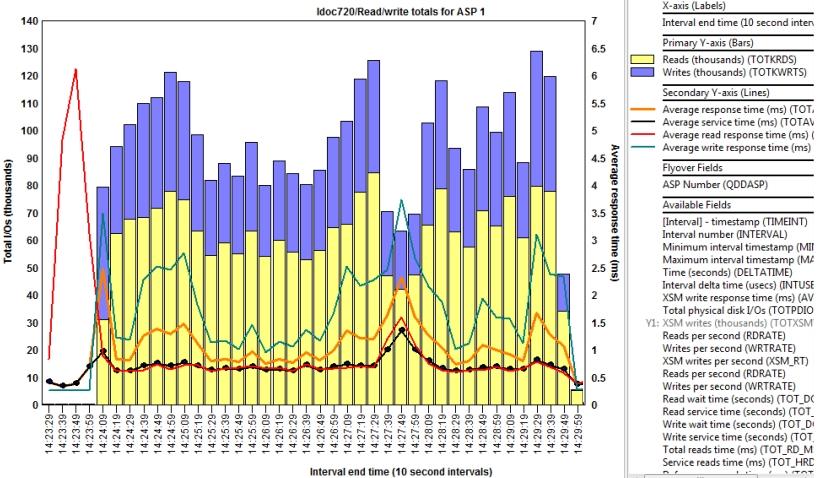
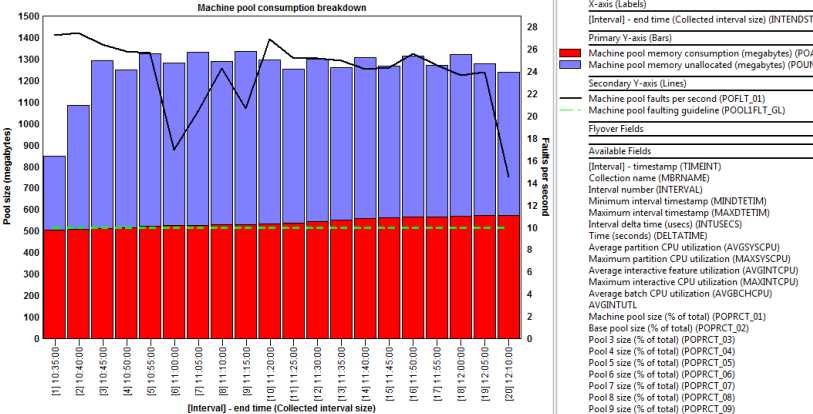
Is it time to upgrade your IBM i Power System? Or do you need to upgrade your IBM i Power System? Most companies upgrade their IBM Power systems on a scheduled interval, but there are instances when response times and throughput bottlenecks cause unacceptable performance levels, and a quick fix is needed. IBM i response times and throughput rely on common system resources and can have a similar effect on performance from an end user experience, but the variables that cause them are very different and are often difficult to figure out. IBM Power system processors, memory, SSD, disk drives...
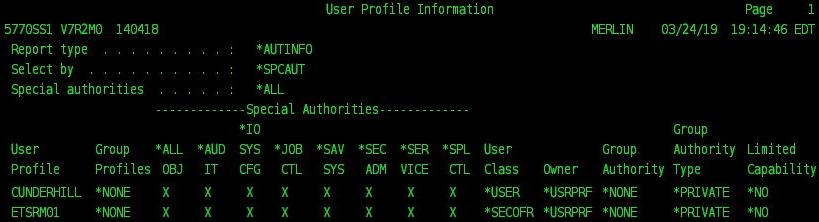
Security breaches making headlines are almost always due to inadequate access controls at one or more levels of a company’s infrastructure. Known and unknown vulnerabilities may have assisted in most security breaches that we read about, but most could have been avoided with the proper security access controls implemented, or at least significantly mitigated. The IBM i security framework is not immune to breaches and certainly not the most secure platform in your environment if the necessary access controls have not been implemented. All compliance regulations have general guidelines to implement various forms of access controls, including stricter authentication policies using Multi-Factor Authentication (MFA), Profile...
Sporadic IBM i performance issues and prolonged degradation that slowly creeps up over time can sometimes be abated by fine tuning memory pools, disk, database, applicatons, jobs and threads, but it’s not a task an untrained administrator should be attempting. IBM i response times and throughput performance issues can be due to numerous factors, and often requires a lot of man hours to pin point by a trained expert. If your IBM Power iSeries already has the Performance Adjuster enabled (view QPFRADJ system value) and other dynamic performance optimization features enabled, it often makes economic sense to simply add memory, disk drives...
IBM SSD Price Drop IBM Solid State Drive SSD prices for iSeries, VIOS and Power AIX systems have dropped so much over the years, making the decision to replace those much slower HDDs very simple. Using Enterprise IBM SSD with eMLC will give queries, applications and other frequently accessed data a significant performance boost. The cost of replacing existing Power system hard disk drives with solid state drives is likely a fraction of what you originally paid for your current hard disk drives. Data you will not likely want to move to Enterprise class solid state drives include sequentially read and rarely accessed...
Database clustering involves database replication to achieve high availability (mirroring, redundancy and disaster recovery), workload balancing for performance or scaling (queries, reporting, business intelligence, analytics and data warehousing), maintenance (upgrades, migration, testing and development), database consolidation and other objectives for data access, efficiency and better decision making. It is use database clustering and replication services where the source and target databases are at different version levels and even different types of databases all together, such as PostgreSQl to Oracle replication, or DB2 to SQL. Database clustering can be implemented for a mix of on premise, virtual and cloud environments, using any...
Database migration and conversion projects can be a time consuming and costly endeavor without the right software, and converting large complex production databases with real-time replication and transformation requirements significantly compound the risks. Using a database migration and conversion tool to map fields of disparate databases correctly and keeping them in sync is key to a successful and non-disruptive conversion. Critical business applications utilizing the database to be converted will add risk to the migration process. Traditional database migration and database converter processes usually take hours or days for large databases, costing businesses unnecessary downtime. Some companies have wasted millions of dollars in...
IBM QRadar pricing is determined by the number of event logs per second and network flow logs per minute the SIEM must ingest. On average, QRadar will replace 6 customer installed security products. Furthermore, QRadar is considered by industry experts to be one of the most advanced and mature SIEM tools on the market, that can also integrate with a customer’s existing security defenses. Volume pricing discounts are provided for all QRadar SIEM product lines, including on premise appliances, software licenses, virtual hardware (any customer provided VMware infrastructure), as well as QRadar SIEM in the Cloud, SaaS and hosted managed SIEM...
New: POWER8 Vs POWER9 Compared for 2020 Even most zero-day exploit attacks can be defended against with proper artificial intelligence, an advanced QRadar SIEM, end point security and a good plan, would minimize or prevent damage to company assets. IBM QRadar SIEM exist because companies discover cybersecurity breaches long after the damage is done. Consequently, in the following weeks and months security personnel and executives will exhaust all resources investigating and responding to the all the events that led up to the attack, and tackle a host of other costly post-incident damage control and prevention initiatives. If the attack was not...
Implementing IBM i Multi Factor Authentication (MFA) and Password Self-Service (PSS) as an integrated solution allows companies to enjoy the cost savings of automation, while enhancing IBM i security and addressing compliance requirements at the same time. On the surface, IBM i MFA, Password Self-Service and 2FA software solutions already have a lot in common. If you are thinking of implementing IBM i MFA, 2FA or Password Self Service, you may want to consider implementing them together to gain both the cost savings and security benefits. CautionWhen buying any IBM i MFA Multi-Factor Authentication, 2FA Two-Factor Authentication or PSS Password Self-Service...
Written by: Bob PiccianoOpen any business publication or digital journal today, and you will read about the promise of AI, known as artificial or augmented intelligence, and how it will transform your business. The fact is, AI will not only transform your entire business, whether you are in health care, finance, retail or manufacturing, but it will also transform technology itself. The essential task of information technology (IT), and how we measure its value, has reached an inflection point. It’s no longer just about process automation and codifying business logic. Instead, insight is the new currency, and the speed with which...