IBM i Profile Swapping for Temporary Elevated Authority
Implementing iSeries Profile Swapping and Adopted Authority policies is a great idea for reducing the number of powerful profiles on the IBM i, especially if most users only need elevated authority for specific tasks or occasional access to sensitive data. On the IBM i (iSeries AS400), the Profile Swapping, Adopted Authority and Elevated Authority procedures are more commonly referred to by compliance regulations and other platforms as Privileged Access Management (PAM) proceedures. However these processes ultimately have the same objective, limiting the number of user profiles on the iSeries that possess unnecessary special authorities (or having a powerful user classes or have no or partial limited capability), and then use policies to grant the required elevated authorities for a specific task or need to access sensitive data that is outside the user’s normal role. Elevated authorities can be granted by several different means on the iSeries, and PAM solutions greatly differ in their flexibility, how they can be implemented and integrated into applications, change management systems and ticketing systems.
When looking at solutions and specifications for Profile Swap, Adopted Authority and PAM requirements, consider your iSeries environment and all external systems and processes you will need to play a role in the end solution. Some likely features needed for a successful PAM implementation may include:
- Integration with Ticket System for end to end management or has built in Ticketing ability
- Integration with SYSLOG Server, SOC or SIEM
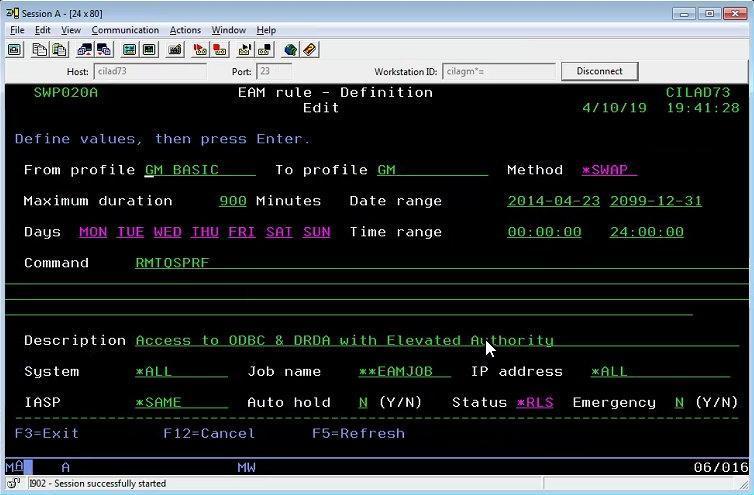
- Ability to use *SWAP and/or *ADOPT
- Control access to menus, specific commands, files, objects, actions, applications, exit points, ports and Open Query tools
- Control amount of time elevated authorities are used
- Automated rules triggered by source User ID, Group Profile, Supplemental Group, user lists and command line access
- Automated rules triggered by day, date range, time, job name, IP address, IASP, Program or other environmental criteria
- Allow Firecall emergency access initiated by specified users
- Log explanation for using elevated authority
- Detailed auditing and reporting: job logs, screen captures, exit points, system journal, database journals, SQL Statements, etc.
- Trigger Alerts
- Integrate with Multi-Factor Authentication (MFA)
- Invoke Four Eyes principle for supervised changes
After this process has been thoroughly outlined, identify the solutions that meet these requirements and conduct a trial or POC before you purchase.
IBM iSeries Profiles with following Special Authorities that should be considered:
*ALLOBJ – can access all system resources, and has authority to all functions on the system.
*SECADM - can create, change and delete user profiles.
*JOBCTL – can end subsystems and shut down system (IPL).
*SPLCTL - can access any spool file on the system.
*SAVSYS - can save and restore any object on system.
*SERVICE – can access sensitive data, use SST, edit programs and change service functions.
*AUDIT – can end auditing on system and for users.
*IOSYSCFG – can change system configuration.
These special authorities are typically only required for specific use cases or tasks. By default, profiles should adopt the minimum authority needed by an application to execute. Best security practices dictate adopting the authority of an application owner versus adopting the authority of a user with special authorities. Unless the individual’s job scope requires elevated authorities, almost all user profiles on your ISeries should have user class *USER. Almost every user profile on the system should have user class *USER, unless their role at the company dictates otherwise. In most cases, users will not require special authorities at all times. Quite often special authorities of user profiles do not match IBM default user class. Other profiles that should be considered for review are users with Limit Capabilities values of *PARTIAL and *NO. Profiles with either of these values can change their initial program, initial menu, library, run commands and circumvent other system controls you may not be aware of.
Please contact us with any questions, to watch a demo or initiate a Privileged Access Management solution POC on your iSeries, or visit the product page for more details.