IBM Power9 Servers may be the best Linux server to run your applications. IBM Power Linux servers have a proven history of delivering over twice the performance per core compared to industry leading x86 server brands. IBM Power Linux servers have also proven to deliver the lowest cost of ownership compared to other Linux servers running on x86 hardware. Although there is no one single answer to this question, the two statements address what most people want to know when comparing Linux server workloads, such as: application server, database server, cloud server, SAP server, analytics server, business intelligence server, web...
SFTP client software or Secure FTP that uses SSH (Secure Shell) and PGP encryption for secure file transfer over the SSH2 protocol as defined by the Internet Engineering Task Force (IETF) SSH (SECSH) working group. Customers with an AS400, iSeries or IBM i can use the Secure FTP (SFTP) to automate secure file transfers to their bank or other trading partners in just a few minutes. Banks like Bank of America, BankOne, CitiGroup, JP Morgan Chase, State Street, US Bank, Vanguard and Wells Fargo have additional file transfer requirements such as PGP encryption, ASCII armored, RSA public key exchange, sign and verify, key...
How to increase IBM POWER System application performance running on IBM i, AIX and Linux Server with SSDs (Solid State Drives) Every IBM POWER System application performs significantly faster running on SSD (microsecond and nanosecond response times, compared to millisecond and seconds). Application performance on IBM POWER Systems experiencing slow query responses times, have intensive I/O requirements or are experiencing latency as a result of accessing data on hard disk drives, can improve performance using various database and query approaches. However, the most effective and usually quickest approach is to replace traditional HHDs with IBM Solid State Drives (SSD) using either Enterprise or...
Managed SIEM Services (MSIEM, SOCaaS, MSSP, SIEMaaS) can provide companies with various levels of security services at a reasonable price including: Monitoring (threat hunting), vulnerability scanningReporting, alertingRoot cause analysisData encrichment and intelligence providing context about security incidentsRecommendations for containment and remediation stepsPerform actual remediation on behalf customerSIEM tuning and managed security services needed to augment deficiencies in expertise and staffing. Managed SIEM prices vary based on the volume of events per second (EPS) and the required level of services from the SIEM as a Service provider. To compare apples to apples, be sure to request a detailed SOW and clear SLA. Outsourcing SIEM...
The IBM Hardware Management Console (HMC) is a virtual hardware appliance used to manage and monitor IBM i, AIX and Linux server workloads running on Power9, Power8, Power7, Power6 and Power5 Systems. The IBM HMC uses built in terminal emulation software to connect and control Power system resources, services, virtualization features and order Capacity Upgrade on Demand. The IBM HMC can consolidate the monitoring and management of all Power systems in a company’s infrastructure that is supported by the HCM code. Every HCM model supports different Power system models based on the version of HMC code. For instance, the latest HCM...
Is your SIEM the magic bullet? Many companies are finding their SIEM implementations have provided little return on investment and have not strengthened their security posture to any great degree. Purchasing the best SIEM and endpoint security tools on the market will not magically identify vulnerabilities, make an infrastructure more secure. Every SIEM requires proper implementation and ongoing tuning services to keep up with the constant changing landscape of threats, vulnerabilities and a customer’s own environment. Like any security product, every SIEM requires an experienced technician to configure it correctly, and enough staff must be trained to keep up with the volume...
It has only been a year, and the new data protection and privacy regulations have already hit a few companies with multi-million dollar fines. Every company with sensitive data on an IBM i (iSeries AS400) and has data protection and privacy requirements, should have implemented DB2 encryption already. Some of the companies seen in the news recently not only failed to secure personal data properly, could not accurately assess how much data was compromised, had a lax incident response plan and were slow to notify authorities. These factors all led to heavier fines, causing the total financial penalties to exceed 100s...
Most SIEM environments rely on a plethora of different servers, storage arrays, hypervisors and network interconnects to support their rapidly growing SOC environments. Likewise, most SIEMs also all have the same issues and concerns about performance, costs and time required to provision and manage storage growth. The primary problem is, the entire infrastructure the SIEM relies on is not integrated or even truly virtualized under a single unified architecture. As a result, administrators are stuck in a never ending battle of upgrading and adding more traditional technology for the same problems, and security analysts are constantly waiting for searches to complete...
Details of each POWER9 and POWER8 hardware enhancement provided by the release of IBM 7.4 (V7R4) are below the initial summary, organized by IBM Power generation and topic. The new IBM POWER9 and POWER8 hardware features provided for OS400 V7R4 are now all available for ordering as of June 21, 2019. Read about IBM i 7.4 (V7R4) announcement details here. IBM V7R4 announcement provides the following I/O enhancements for Power9 scale-out and scale-up system models: 1.6 TB, 3.2 TB, and 6.4 TB PCIe3 Enterprise SSD NVMe adapters for Power9 E980, E950, L922, S922, S914, S924, H922, and H924 servers1.6 TB and...
QRadar Prices for All-in-One SIEM Appliances start at $38,500.00 to $102,000.00. Pricing is calculated based on the volume of events and network flows ingested by the SIEM. QRadar prices for All-in-One appliance includes the following licenses for out of the box deployment: Maximum Events per Second defined by model (expandable increments: 100, 500, 1000, 2500, 20000, 40000, 80000)Maximum Flows per Minute defined by model (expandable increments: 10000, 25000, 50000, 100000, 1200000, 2400000, 3600000)QRadar Security Intelligence Console for SOC including advanced threat protection, predefined dashboards, partner provided and editableIBM Security AI Sense Analytics for assets on premise, mobile, remote sites and cloud servicesAsset...
This QRadar vs Splunk comparison will help anyone planning on switching in 2019 from Splunk to QRadar SIEM. It will also help anyone just curious to s...
This specification breakdown of the IBM Power9 9009-42A model S924 will explain the key performance features that sets it apart from its Power8 predecessor. In comparison to the 8286-42A model S824, the IBM Power9 S924 delivers 40-50% better performance for data intensive database and analytics workloads, with over twice the memory footprint (accelerated by Coherent Accelerator Processor Interface CAPI) running at speeds up to 344 GB/s (172 GB/s per socket), has over 60-70% more CPW for IBM i workloads and 2X the I/O bandwidth (Gen4 PCIe slots). IBM Power9 with CAPI 2.0 increased I/O bandwidth over 4X Power8 ability, clocked at 192...
A hyper converged infrastructure (HCI) uses software to virtualize all server and storage resources for streamlining, automating and maximizing IT resources and operations for a variety of complex, compute-intensive Databases, VDI, Microsoft, Business Applications, Cloud, Big Data, SIEM, SYSLOG and other x86 environments. HCI virtualization solutions significantly reduce operating and licensing costs, provide predictable performance, provide up to 2.8 times storage gains and enables long-term flexibility and scalability. The HCI software defined infrastructure model addresses almost every IT challenge facing companies today, including:Improving IT staff productivityImproving operational efficiencyReducing capital expensesReducing operating expensesImproving backup/recoveryImproving resource utilizationData center consolidationThe value of hyper converged infrastructure...
Configuring the IBM i to forward security and system event logs to QRadar SIEM can be done a few different ways, but in order to do it correctly; in LEEF format, in real-time, with GID and enriched event log information, you need an IBM i event log forwarding tool designed for the QRadar SIEM. There are IBM i security event log forwarding tools that can be used for QRadar that will send event logs in real-time and in CEF SYSLOG format, and even a couple that support LEEF, but only one includes QRadar QID for mapping, log enrichment and is on...
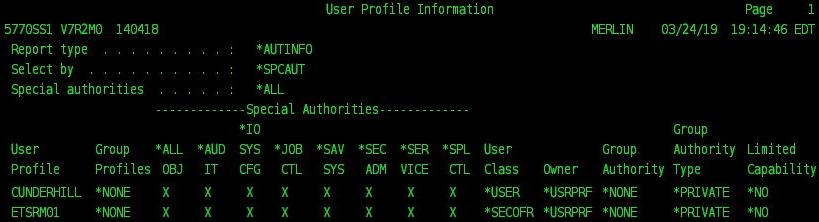
IBM i Privileged Access Management (PAM) solutions have various levels of flexibility for implementation and integration with existing applications and ticketing systems that need to be considered before purchasing. Assessing your IBM i Security requirements for implementation will be key to ensuring the IBM i PAM solution you choose meets your all your use cases, as well as environmental and compliance requirements. First note, Privileged Access Management (PAM) terminology used by most technology sectors and compliance regulations refer to processes more commonly known on the IBM i (iSeries AS400) platform as Profile Swapping and Adopted Authority procedures. Terminology aside, the goal of...
IBM i customers upgrading to a new IBM Power9 scale-out system from an older Power system have three models to compare specifications; the 9009-41A S914, 9009-42A S924 or 9009-22A S922. Before jumping to any conclusions about which Power9 system is right for you, consider the specifications and resources of your current IBM i and performance during peak times. The new Power9 systems are so powerful, many companies are finding they can drop a software tier without any question. Dropping an IBM P-Group in itself is a significant cost savings, and the total cost of ownership price tag adds up after factoring...
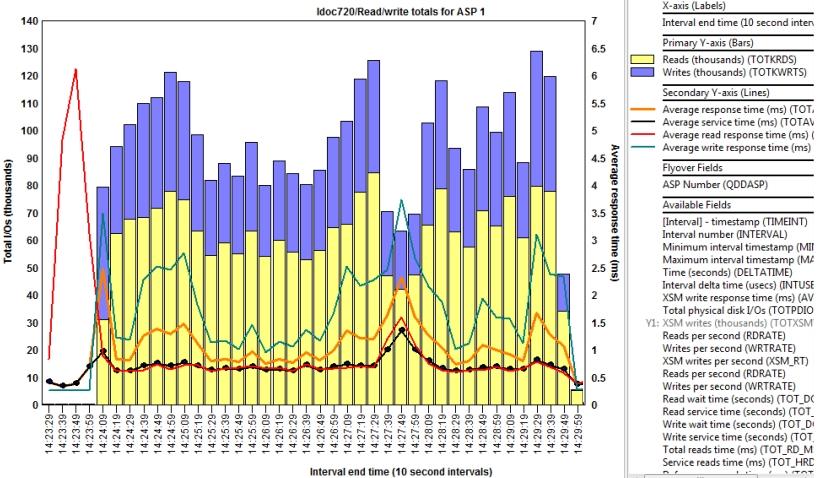
Keeping your IBM i optimized for optimal response times requires regular monitoring of system resources and identifying various elements that affect application performance. Poor response times of only two or three seconds delay can quickly get compounded over time when poorly written applications are involved or database maintenance has been neglected. Like most performance degradation issues on the IBM i, response time issues only get worse as the number of transactions multiply. Ignoring system performance issues affects productivity and frustrate customers, which in turn increases costs and affects revenue. Below are some ideas to consider if a major IBM i upgrade...
*Also see QRadar Pricing on all IBM SIEM Security Intelligence Product Prices (including QRadar Hardware Appliances) QRadar SIEM Free Trial Compared to what you are doing today, QRadar will unify your existing IT infrastructure and security products into a user friendly and intelligent SOC. QRadar provides advanced, automated threat detection above and beyond what you would expect. But the only way to appreciate the simplicity and robustness of QRadar SIEM platform is to evaluate security solution for yourselves. QRadar FREE Trials & Demos 2023 QRadar Manufacturer Suggested Retail Price Chart by License*MSRPQRadar SIEM by IBM Security - Event Processor Virtual 1690...
IBM EJ14 PCIe3 12 GB Cache RAID Plus SAS Adapter is the highest performing raid controller (SAS adapter) for IBM Power9 and Power8 systems that will significantly improve raid performance. The IBM EJ14 PCIe3 12 GB Cache RAID PLUS SAS Adapter has four 6 Gb connectors enabling the highest performance HDD or SSD SAS controller capabilities for IBM Power systems using PCIe Gen3 technology and IBM’s latest SAS RAID adapter technology. The EJ14 PCIe3 SAS adapter builds on the success of the EJ0L PCIe3 12 GB Cache RAID SAS Adapters, but delivers up to 100% more write IOPs than the older EJ0L...
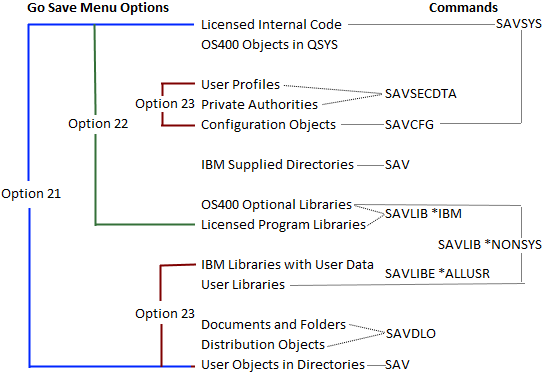
IBM i backup performance is affected by many variables, and many data transfer rate bottlenecks can be very easy to resolve. Some simple changes you can try to improve backup performance may only require using the correct media generation for your tape library/drive, minimize resource sharing, shortening the distance between the IBM i PCIe I/O adapter and tape library/drive, using backup optimization settings or restructuring your backup processes. These minor changes are virtually free to try and may have a significant impact on optimizing your IBM i backup transfer rates and without having to spend a lot of time analyzing the...