iSeries Profile Swapping Elevated Authority IBM i AS400 Adopted Authority
IBM i iSeries Profile swapping and adopted authority policies provide AS400 users with temporary elevated authority to perform tasks or access sensitive data based on User ID or Group policies, which automatically grant required authority based on: predefined rules, ticket systems, user initiated requests, manually granted, according to date and time range parameters, and can incorporate various other requirements such as IP address, job name, duration, status and severity. Using IBM i iSeries profile swapping allows administrators to reduce the number of powerful user profiles on a system, while providing automated and flexible rules that issue elevated authorities when user tasks requires them. Note: most compliance regulations and other technology sectors refer to Profile Swapping, Adopted Authorities and Elevated Authority functions as Privileged Access Management (PAM) solutions.
The Elevated Authority Manager for IBM i also allows rules to be defined for adopting authority instead of swapping to a more powerful profile. The Elevated Authority Manager includes many auditing, monitoring and reporting features to track profile swaps, including; screen capture, alerts, detailed job and audit logs using QAUDJRN, database journals and exit programs. Elevated authority’s policies for profile swapping and adopted authority support management functions from a graphical console or 5250 green screen menus.
Using profile swapping and adopted authority policies provided by the Elevated Authority Manager gives administrators complete control of OS400 user authorities to meet the most stringent regulatory requirements mandated by PCI-DSS, HIPAA, GDPR, SOX and other compliance regulations. Reducing the number of powerful user profiles and limiting user access to sensitive data are also added benefits for a more secure system.
How the Elevated Authority Manager EAM Works
When a user requires elevated authority for a specific action, they ask for elevation of authority within their job, requiring a specific profile and the command to be run. Requests can be accepted by the administrator, or configured to automatically grant requests based on rules defined by the administrator.
EAM’s powerful rules are defined for pairs of requesting and requested profiles based on group profiles, supplemental groups, lists of users and command line access. Rules provide the context around which requests can be granted, including day of the week, date range, time range, job name, IP address, IASP and more. They also determine whether profile swapping or adopted authority methods will be used for elevating authority and the duration of the elevation. EAM can also be instructed to log all user activity without changing the user’s authorities.
If the request meets the rules defined, it grants the user’s job the authority of the target profile, launches the initial command, places the job under its control and starts logging job activity. Multiple sources are used to log activity including job logs, screen captures, exit points, and system and database journals to ensure a complete audit trail is captured. When the command completes, EAM restores the authority of the initial profile, stops logging the job activity and records the log. EAM also controls how long the job runs with the authority of the target profile. If a job exceeds its duration, EAM alerts the user. Based on rules configuration, the job can then be held or canceled.
Key Features
- Offers users a fast and easy process for requesting authority
- Allows authority requests to be granted manually or automatically based on rules
- Enables powerful rules to be defined for source and target profiles based on group profiles, supplemental groups, lists of users and command line access
- Rules determine the context around which a request can be granted, including day of the week, date range, time range, job name, IP address, IASP and more
- Rules define whether *SWAP or *ADOPT methods are used for elevating authority
- Provides a *JOB option that logs all user activity without changing the user’s authorities
- Supports external processes connecting through ODBC, JDBC, DRDA and FTP
- Maintains a complete audit trail of activities from elevated profiles based on multiple sources, including job logs, screen captures, exit points, and system and database journals
- Supports management from a graphical console or full-featured 5250 menus
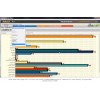
- Displays currently elevated users and duration of elevation in a graphical dashboard
- Provides ability to drill into logs of statements executed and view scree captures of activity
- Able to enrich job logs witih SQL statements, FTP functions and critical commands
- Allows rules management to be delegated with a complete audit trail and segration of duties
- Delivers alerts on events, such as exceeding authorized time, via email, popup or SYSLOG
- Logs and reports on all requests with customizable filters
- Produces reports in PDF, XLS or CSV formats
- Can be integrated with 3rd party helpdesk solutions and ticketing systems
- Event logs can be forwarded to SIEM Security tools