iSeries AS400 Encryption for IBM DB2 database field column row
The iSeries Encryption, Masking and Scrambling module utilizes IBM i FIELDPROC feature of OS400 and provides an intuitive GUI interface that walks you through the encryption of DB2 database fields in a couple minutes. IBM i Encryption adds a critical layer of protection for sensitive data, and is required for many compliance regulations. Even when encryption is not mandatory, companies should use common sense when determining when data should be protected with encryption, masking or scramling. The IBM i encryption feature is an extension of the iSeries Enterprise Security suite, but can also be purchased separately. Our IBM i encryption solution requires no source code changes and works no matter how your iSeries data is accessed or where it resides, such as when presented in third party applications, or when being replicated, backed up, stored in journals, printed or any other means used to store or access the encrypted data.
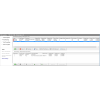
iSeries Encryption, Scrambling and Masking features for DB2 Database
Encryption: encrypts both numeric and alphanumeric fields in DB2 database using an encryption algorithm of your choice (AES 256, AES 192, AES 128, TDES 24, TDES 16, TDES 8, DES). Unauthorized users will not be able to see the encrypted data, regardless of where your data is stored or how it is accessed. Using universally accepted PCI approved encryption algorithm standards.
Field Security: prevents updating fields while allowing read access unrestricted.
Masking: replaces all or selected positions of a field on the fly, before displaying the data to the requester. Changes to field take place at the time of the record read, and the DB2 field remains unchanged.
Scrambling: applies an arithmetic function on all or specified positions of a field on the fly, before displaying the data to the requester. Changes to field take place at the time of the record read, and the DB2 field remains unchanged.
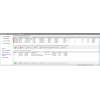
Full or partial masks of fields can be applied on any kind of database field. For numeric fields, you have the option to scramble data, which is ideal for data used in development and testing applications.
RCAC Field Masking: performs field masking using Row Column Access Control feature available in OS400 V7R3 or later.
IFS File Encryption: encrypts any object in the IFS.
Save File Encryption: replaces a SAVF object with an encrypted file, and cannot be used on any system until safe file is unencrypted. Good for encrypting files for backup.
Key Management: flexible key management, providing two-tier encryption requiring master keys in order to generate data keys, ensuring strict separation between those who generate keys and those who use them, and keys can also be encrypted. Encryption keys can be stored on IBM iSeries or on a remote server. Encryption keys are assigned to users or groups of users based on roles defined by the administrator. An unlimited number of encryption keys can be created, and a different encryption key can be used for every field. Encryption key strings (characters used by algorithm), can be entered manually or randomly generated so that even the administrator does not know the encryption key.
User-defined Access: allows for decrypting data for groups of users, without the need for application level detail.
High Availability Compatibility: Encryption works in high availability environments without any special measures being taken. Backups and replicated databases will be identical to the production system and will contain the master and data keys needed to encrypt and decrypt the data.
Back-Up Encryption: object encryption for backups, providing ability to encrypt and save entire libraries as well as individual objects. A series of commands allow easy integration of object encryption into back-up processes. Organizations backing their data up to tape, now have an easy way to make sure the data cannot be read by anyone who is not authorized in case their tapes end up in the wrong hands.
Data Protection: Encryption adds a vital layer to the security of an organization's sensitive data. Enforcive provides GUI-Managed File and Field Level Security, preventing even Power Users from accessing data in fields that require limited access.
Application Independence: Field Encryption has been engineered to minimize impact on mission critical applications that could be affected by a encrypting and decrypting processes. Existing database file structures remain unchanged. Organizations will typically not require any program changes.
Compliance: Requirements such as the PCI Data Security Standard (requirement 3) specifies protection of stored cardholder data. Enterprise Security provides the ultimate answer to that requirement by a foolproof encryption and decryption mechanism using universally accepted PCI approved encryption algorithm standards.
Reports: With the existing features provided by the Enterprise Security product including Exit Point Management, Object Authority Management and IP Packet Filtering, Enforcive offers the ultimate tool for data protection.