iSeries SIEM SYSLOG forwarding software
iSeries SIEM converts and forwards any AS400 event log into CEF format with key value pair data in real-time or in scheduled batches. Supported iSeries event logs include: system security journal (QAUDJRN), receivers (journaled DB2 database files), exit point logs (applications access system), history log (QHST), message queues, SQL audit, IFS and encryption log. IBM iSeries logs are converted and forwarded to your SIEM or SYSLOG Server in Common Event Format CEF or SYSLOG with Key Value Pair KVP associations for automatic parsing. Configuration and forwarding can be setup in under a minute, with option to send all or user defined event logs to your SIEM or SYSLOG Server.
Some of the more common SIEM and event log management tools supported are: QRadar, Splunk, McAfee, LogRhythm, Solarwinds, Alert Logic, RSA enVision, HP ArcSight, AlienVault, Kiwi, SYSLOG NG and any other logging tool that supports Common Event Format “CEF”, custom CEF “CCEF”, NFX and like industry formats. The robust filters allow you to control which events get forwarded or omitted from your IBM iSeries, as well as including or suppressing user groups, which will minimize impact on your system resources, disk and bandwidth utilization. The SIEM and SYSLOG forwarding tool can send IBM iSeries event logs in real-time or in scheduled batches. All IBM iSeries event types are supported and converts all event logs into a format your SIEM SYSLOG Server can read and parse properly. Installation and configuration is provided for free, including for trial evaluations "POC".

IBM iSeries event log types (Data Sources) that can be forward to your SIEM or SYSLOG Server include:
- System Audit Journal "QAUDJRN"
- Database Changes & Reads "Journaled DB2 file access including before & after images"
- SQL Statements "Interactive SQL, QSHELL database functions, embedded SQL and Queries"
- Network Events "Exit Program" such as FTP, ODBC/JDBC and other Applications providing access via TCP/IP
- History Log "QHST"
- Message & Job Queues
- Logs stored on the IFS
- Intrusion Detection Alerts
- Any otherevent or log from your iSeries
Midland's security system can send any IBM iSeries, Power AIX or OS390 Mainframe system log event to any SIEM or SYSLOG Server that supports Common Event Format “CEF”, custom CEF “CCEF”, NFX and other accepted industry formats, including Splunk, McAfee, HP ArcSight, IBM QRadar, Kiwi, Solarwinds, Alert Logic, RSA enVision, LogRhythm, Secure Analytics, netForensics, WinSyslog, WhatsUp Gold, Novell, Syslog NG and Cobrasonic.
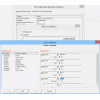
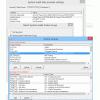
SYSLOG Collection Criteria: Midland's security system can pre-filter iSeries events for each Data Source to prevent sending non-relevant data using a number of selection criteria and/or using boolean expressions to define your selected event types. For example, with extraction of events from the IBM Audit Journal you can specify to include or omit specific groups of users, choose which of the IBM audit journal types are relevant to your extraction and even which groups of objects the events should relate to. Similarly with Application Audit, the administrator can choose which exit point (application server types, such as FTP, ODBC/JDBC) events are sent to your SYSLOG server, and whether only violations should be sent or all. For further filtering of the events, a Query Wizard is available to define the extraction, such as events relating to libraries beginning with Q*, or generated by a specific group of jobs.
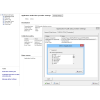
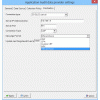
Tailored for SYSLOG and SIEM frameworks: All the administrator has to do is choose where to send the extracted iSeries event logs by entering the IP Address and Port of the SYSLOG or SIEM server, as well as the desired format. Midland's security system can send IBM iSeries events fto any SYSLOG or SIEM Server for analysis. Midland's security system has created specific processing formats for RSA enVision, ArcSight, Netforensics and Nitro Security. Other SYSLOG Servers and SIEM tools that utilize a more standardized SYSLOG formats such as Kiwi, Splunk, SolarWinds, WinSyslog, WhatsUp Gold and other tools will conveniently work using the standards based format. Events can also be sent to the Cross Platform Audit log management and archiving. The CPA is an ideal tool where IBM platforms and databases need to coexist with other platform and database types within a single repository for audit log archiving and analysis.
Don't have a SYSLOG Server yet? You're lucky! Check out Midland's security system's Cross-Platform Audit "CPA" and compare the differences for yourself. The Midland's security system CPA is ideal for consolidating Database, System and Security event logs from any platform efficiently. The Midland's security system CPA lets you define custom data extraction policies for each event source by event type and/or user before extraction into the Midland's security system Sequel Database. Midland's security system's CPA supports:
- IBM iSeries: System Audit Journal "QAUDJRN" | Database Changes & Reads "Journaled DB2 files" | SQL Statements | Network Events "Exit Program" such as FTP, ODBC/JDBC and other Applications | History Log "QHST" | any Message & Job Queue
- IBM Mainframe: SMF Telnet, SMF FTP, SMF VSAM, SMF RACF | TCP/IP FTP, TCP/IP Telnet applications | DB2 SMF, DB2 Data Audit Log, DB2 CICS SQL Data Capture, DB2 Batch SQL Data Capture
- IBM AIX: System Audit & DB2 Database File Audit
- Windows: System Event Logs, Applications, DNS and others | Active Directory Compliance | ISA Server Logs | DHCP Logs, IIS Web Server Logs & Exchange Server Logs
- Linux: System Audit X86, 86_64, IA64, PPC64, PPC, S390X, S390
- Unix, Solaris: System Audit
- SYSLOG sources & devices: Routers, Firewalls, Antivirus and any other SYSLOG source
- Oracle: SQL Statements, Oracle System Logs, Admin Logs, Users/Profiles, Procedures and Database Audit
- DB2: File and Field Audit with Before/After Images side-by-side
- MS SQL: SQL Statements, System Audit and Data Audit
- MYSQL: Audit, Connect, Query, Prepare, Execute, Shutdown, Quit, No Audit Init DB and others
- Progress: System Audit & Data Audit
- SYBASE: System Audit