AI Security SIEM QRadar Machine Learning User Behavior Analytics
AI security SIEM utilizes machine learning, cybersecurity threat feeds and user behavior analytics to detect risky and abnormal activities which can automate many difficult to produce and time consuming manual tasks of threat hunting. In data centers where security risks and costs are rapidly rising, AI security for SIEM tools provide very cost effective and efficient means to identify insider and cybersecurity threats around the clock without any additional expense. Over half of all security breaches are caused by trusted employees that either inadvertently or maliciously taken part in a attack, causing data loss, compliance violations, destruction of systems and other serious and expensive consequences. Insider user threats are notoriously harder to detect because they require a deeper analysis of user behavior to expose, which perimeter defense and vulnerability scanners using simple algorithms cannot accomplish. Most insider threats are not disgruntle employees, but are genuine user mistakes that make them victims of phishing scams.
User Behavior Analytics is one of several features included with QRadar SIEM Security which other security information event management tools either charge extra for or require a third party solution provider to facilitate. User Behavior Analytics (UBA) uses AI security and machine learning technology to analyze user event and network flow logs to distinguish between normal and abnormal user behavior, identify early warning signs of irregular user actions, categorize risky user behavior and provide security analysts with the tools they need to prevent costly damages. Given the context in which users can be determined as an internal threat, the UBA’s analysis includes the following criteria for examining user behavior:
- User’s access location
- Time of day of login
- Change in account usage
- Change in account privileges
- Frequency of privilege use
- Access to valuable assets
- Amount of data sharing
- Communication with external systems
- Per group outliers
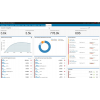
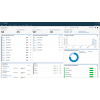
Out of the box, the UBA application is able to assess a base line of normal activity within 24 hours, provides rules and algorithms that can be used with QRadar’s advanced analytics engine, and enhances event logs, flows and vulnerability data with user context data. QRadar UBA can assess user patterns and activities to quickly identify risky users, rate your users and provide security analysts with added context related to specific incidents when additional insight is needed. Assessing users high risk activities help security analysts pin point specific insiders that have engaged in unauthorized activity or likely had their credentials compromised. UBA is also integrated into QRadar’s incident response solution, which automates proactive processes that reduce the amount of time needed to contain, remove and recover from an insider threat.
UBA has a dedicated dashboard in the QRadar console that illustrates user data by risk associations, incidents and offenses generated, user risk score, user activity origin and machine learning status. Assessment results can be drilled down into for detailed view of a user and their associated incidents and offenses. The QRadar User Behavior Analytics app was built to detect anomalies in user activities using behavioral rules and analytics to detect changes in user behavior and deliver continued visibility and tracking of their activities. UBA automates the required monitoring, detection and investigation of user activity, to help security analysts become more efficient and successful, while also reducing alert fatigue.
Security AI and Machine Learning
QRadar UBA comes with advanced behavioral analytics and machine learning algorithms that augment the robust analytics engine within QRadar SIEM. These algorithms are packaged and delivered in the Machine Learning (ML) App, which comes bundled with QRadar UBA.
Over half a dozen machine learning algorithms in the ML App analyze users’ activities and creates a behavioral model for each individual user. The app ingests users’ log data from the preceding 4 to 6 weeks, and within hours of installation, it understands the normal activity patterns of each monitored user. These algorithms are then able to predict users’ future activities and the frequency of those activities. When a user’s activities fall outside of the predicted range, the algorithms flag these activities as anomalous behavior.
Security analysts can dynamically scale the risk score assigned to users depending upon the magnitude of a users’ deviation. So a user who deviates within 1 standard deviation from the normal may get 5 points, but the user who deviates 2 standard deviations may automatically be assigned a risk score of 10 points. The machine learning algorithms in QRadar UBA can be used for:
1. Detecting Users’ deviation from themselves
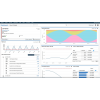
The multi modal Gaussian analysis in the QRadar UBA app monitors users’ behavior across multiple categories of events. A user’s behavior is modeled in 18 different categories of user activities, such as authentication, network access, firewalls accept/denies, application activity, port or network scans, denial of service type events, malware or other malicious software activity etc. Figure 3 shows the 18 categories of activities modeled by these algorithms.The anomalies detected by these algorithms are displayed in the form of spider charts (Figure 3) for all categories of events that the user has shown activity. Examples of anomalies that can be detected include:
- Abnormal increase in user activity level (over time)
- Deviation in a specific type of user activity, such as an increase in authentication requests
- Deviation of the user’s risk posture
- Abnormal rate of increase in the user’s risky activity
- Deviation or increase in a user’s local to remote activity (helps detect exfiltration activities)
- Changes made to a user’s systems, software installation etc.
2.Detecting change in user’s activity vs. frequency
QRadar UBA takes these machine learning algorithms a step further to understand the detailed mix of activities that a user may be engaged in and the frequency of each of these different types of activities at any given point time. Leveraging Latent Dirichlet allocation and Kullback–Leibler divergence, QRadar UBA creates an activity and frequency distribution model over time for each user. ie. a user’s activity with a frequency distribution over one week. Any time the user’s activity or the frequency of that activity changes (the actuals deviate from the predicted values of the algorithm), it is flagged as an anomaly.
These algorithms can help detect instances when a user’s credentials are compromised or when a user with legitimate credentials changes the frequency of certain tasks he or she regularly performs. Examples of the anomalies that can be detected are:
If a person with the stolen credentials engages in different types or patterns of activity, the algorithms would immediately detect the change in activity and increase the user’s risk score
If an internal user (an employee or contractor) with legitimate credentials changes the frequency of his/her normal activity, (increased access to or download from a regularly-accessed asset) this change will be detected and the user’s risk score will be raised.
3. Anomalous deviation from Peer Groups
The above referenced algorithms and analytics are very effective in understanding each individual user’s behavior and detecting any time the user deviates from their normal known behavior. The third set of machine learning algorithms in the QRadar UBA take these individual users’ behavior models and create behavioral clusters of similar users.
These algorithms leverage Gaussian mixture, Jaccard similarity to identify and cluster users into peer groups of users with similar activities. It then uses Kullback–Leibler divergence to detect when a user deviates from his or her peer group to sense any anomalous activity. Figure 5 shows a user’s activity and their deviation from the peer group, along with the names of members of this peer group. Any time a user deviates 1 standard deviation from the peer group’s normal, the app raises an anomaly and raises the users’ risk score. Peer group analytics give yet another lens into a user’s activities and helps identify anomalous or malicious activity when the user deviates from a peer group of employees with similar roles and responsibilities.
Prioritize users and assets
The QRadar UBA app can prioritize both users and assets with a higher risk profile, so security teams can respond quickly to the most critical issues. Out-of-the-box rules and analytics can be customized to fit the unique requirements and risk profile of your organization. The app also enables security teams create their own rules based on organizational policies, such as segregation-of-duties and user access permissions.
Let’s say an organization wants to get a handle on its privileged user activities. QRadar UBA can monitor for anomalous access by privileged users—such as the first time they access a high-value system; access during unusual times or from unusual locations; or access from a canceled, suspended or closed account. The solution can prioritize the alert on the dashboard and notify the SOC analyst so he or she can begin investigation and take appropriate remediation action.
More importantly, organizations need to be able to detect and prevent the use of stolen credentials – particularly privileged credentials. QRadar UBA can monitor for abnormal changes in account usage—such as multiple login failures; access using rarely used privileges; time-space disagreements (logging in from two different locations at the same time, for example); or account usage deviating from peer group behavior (such as making large data transfers during off-business hours, for example). Each of these anomalies can indicate that a privileged user’s credentials have been compromised and are actively being used by a remote bad actor. QRadar UBA can prioritize these alerts to rapidly notify analysts of a potential compromise.
Respond to Insider Threats Faster
Detecting threats early in the attack cycle is a critical step in stopping attackers before they take off with your sensitive data or wreak havoc on your IT systems. Yet, it’s only the first step. The IBM Security Intelligence Platform offers add-on apps and out-of-the-box integrations with complementary solutions to help analysts accelerate investigation times, contain attacks faster and more quickly recover from incidents.
- QRadar Advisor with Watson uses cognitive intelligence to help security teams dramatically accelerate investigation times. When a threat is detected, analysts can use QRadar Advisor with Watson for further analysis. Operating up to 60 times the speed of manual threat investigations, it helps show the scope of an attack, uncover new threat patterns, triage threats and identify the root cause of an attack.
- i2 Analyze enables security analysts to visualize activity associated with an incident and easily share analysis with fellow team members. Analysts can map out high risk users, their relationships with the organization and the actions they’ve taken leading up to and following an incident.
- Identity Governance and Intelligence shares information on user groups and user entitlements, providing context to user behavioral patterns, and can receive information regarding high risk users and activity. When a user engages in a particularly high-risk activity, the solution can be notified of the activity and automatically suspend the user’s account access to avoid further damage.
- Resilient Incident Response Platform enables security teams to orchestrate and automate incident response processes. When insider threats are detected, security analysts can use pre-defined playbooks to orchestrate the response, contain the threat and quickly recover from the attack.
QRadar SIEM Demonstration
QRadar SIEM with integrated Cybersecurity AI
How QRadar SIEM Security is Different from other SIEM Tools
QRadar SIEM Security AI with Watson Advice
QRadar AI Security Machine Learning User Behavior
QRadar SIEM Security Commercial
QRadar SIEM Security Introduction
QRadar SIEM Security Free Apps for Integrating Cisco Security
QRadar SIEM Security Free Apps for Integrating VMware Security
QRadar SIEM integrated Cybersecurity AI - Am I affected Example
QRadar SIEM Machine Learning User Behavior Analytics for Internal Threats
QRadar SIEM Incident Forensics to Stop Security Breaches
SIEM Security and Patch Management are 2 Peas in the same Pod
QRadar SIEM Security as a Service (In the Cloud)
QRadar SIEM Security for Cloud Environments
QRadar using Watson Cybersecurity AI Discovery Service
IBM Managed Security Services MSSP SOC
QRadar SIEM Helps Secure City Government with few IT Resources
QRadar SIEM with embedded Security AI DS
QRadar SIEM Security Machine Learning User Behavior Analytics DS
QRadar SIEM AI Cybersecurity Threat Feeds xForce
QRadar SIEM Security User Behavior Search Analytics DS
QRadar SIEM Vulnerability Scanner DS
QRadar SIEM Security xForce App Exchange DS
SIEM Security MSSP SOC Service Offerings
SIEM Security Product Comparisons
QRadar Scaling, HA, DR Protection
QRadar SIEM Security Customer Feedback
SIEM tools and Security AI Integration WP
Finding Cybersecurity Threats Efficiently WP
AI in Cybersecurity for Security Automation WP
How to Detect and Stop Cybersecurity Threats
Cybersecurity Breaches and Data Theft Cost Study 2018
QRadar SIEM Security Wimbledon CS
QRadar SIEM Security Cargills Bank CS
Optional Add-on Licenses and Services
QRadar SIEM Security Product Line
QRadar SIEM Security Executive Guide
End Point Security Patch Automation DS
End Point Security Patch Automation WP
End Point Security Patch Automation CS
Software License Inventory Management DS
Software License Inventory Management WP
Software License Compliance DS
Software License Compliance WP
QRadar SIEM Cybersecurity Breach Watson Analysis
QRadar SIEM Security Network Traffic Analysis DS
QRadar SIEM Security Network Traffic Analysis WP